Multifactor authentication (MFA), commonly referred to as two-factor authentication or 2-step verification, plays a crucial role in online security and is one of the best things you can use to safeguard your data. It goes beyond mere passwords, adding an extra layer of protection that makes it much harder for cybercriminals to gain access to your personal accounts. In this guide, we’ll explore the world of MFA, its benefits, and how you can easily set it up to enhance your online security.
What is multifactor Authentication (MFA)?
So, what exactly is multifactor authentication? In simple terms, it’s a security measure that requires you to provide multiple pieces of evidence to verify your identity before being granted access to your accounts or data. MFA is necessary because passwords alone are no longer sufficient to protect online accounts. With the increasing number of data breaches and sophisticated hacking techniques, enabling MFA is no longer optional; it’s a requirement.
There are three common forms of authentication factors:
- Something you know: This is typically a password or PIN code.
- Something you have: This could be a physical device like a security key or a digital item like a one-time code sent to your phone.
- Something you are: This is a biometric factor like a fingerprint or face scan.

Source: Pixabay
Why is MFA important?
Let's take a closer look at the key benefits of using MFA. First, it significantly reduces the risk of unauthorized access. Passwords can be guessed, hacked, phished, or socially engineered quite easily these days. But when using MFA, even if someone manages to find out your password, they would still need the additional factor to gain entry to your account.
This additional step makes it much harder for hackers to compromise your accounts. Additionally, according to Microsoft, implementing MFA can make you 99% less likely to get hacked. So, it’s good practice and a great habit to get into for both your new and old accounts.
Second, MFA can safeguard your accounts even if your password is leaked or stolen; it protects against phishing links, keylogging, brute force attacks, password database leaks, and more. With just a password, hackers have free reign to exploit your data. However, when MFA is enabled, they’ll be intercepted unless they also possess the second factor required for authentication, which in most cases will be highly unlikely.
What are the different types of MFA?
There are several options available for the second factor in MFA that are dependent on the service being used; each one is different. Here are the most common options available:
- SMS code: The system texts a one-time passcode to the user's mobile phone. This is convenient but less secure than other methods.
- Authenticator app: The user gets a time-sensitive code from an app like Authy, Microsoft Authenticator, or Google Authenticator. This is one of the most secure and popular options, especially since many let you use biometrics to log in for extra security.
- Security Key: The user inserts a physical key like a YubiKey or OnlyKey into their computer when prompted. This is very secure, but it’s less convenient than an app and can be easily lost.
- Biometrics: The user provides a fingerprint, facial recognition, or other biometric factor. This is especially convenient for mobile devices, but it’s not available everywhere.
- Email code: A one-time code is emailed to the user. This is less secure than other methods but useful as a backup.
- Push notification: The user approves the log-in via a simple push alert to their phone. This is easy to use, but it only works on mobile devices.
- Phone call: Similar to an SMS code, the system instead calls you and speaks out a one-time passcode once you pick up the phone.
As you can see, authenticator apps and security keys provide the best security, while SMS, email, and push notifications are the most convenient and favor usability.
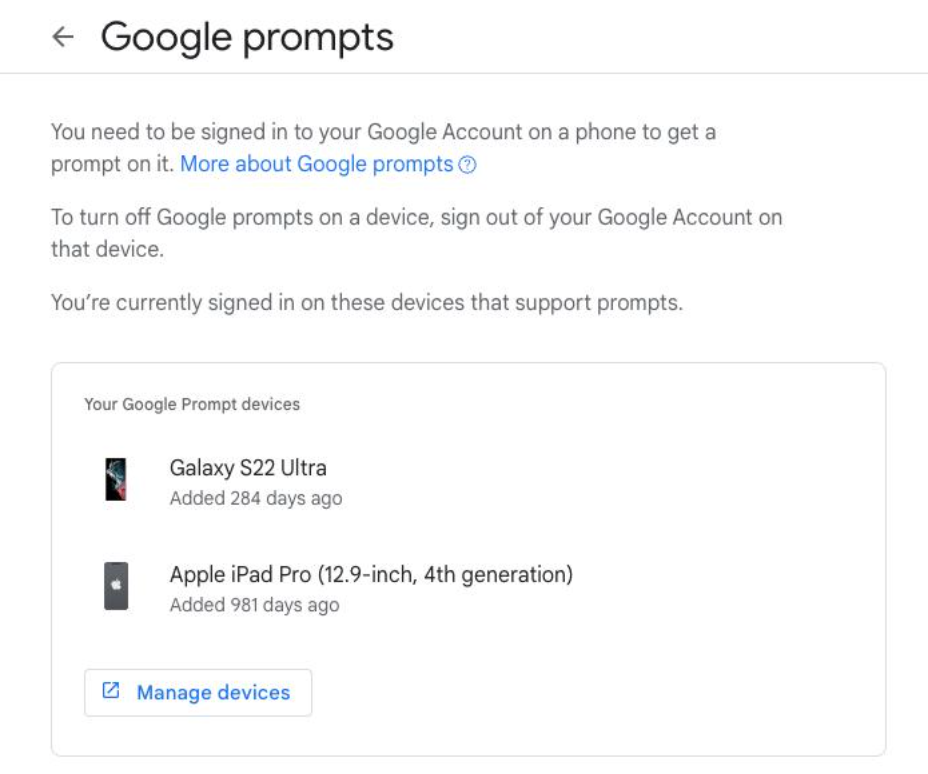
How do you enable MFA?
The good news is that many services and platforms now offer MFA as an option. If you go to your account settings, you can usually find it under the "security", “two-step verification,” or “two-factor authentication” sections. From there, select the option to enable MFA.
Most commonly, you’ll find it in the form of an SMS code or push notification sent to your mobile device. This acts as the second factor and is valid only for a limited period of time. In addition to these, you’ll often have the option to set up an authenticator app that generates unique codes for each login attempt.
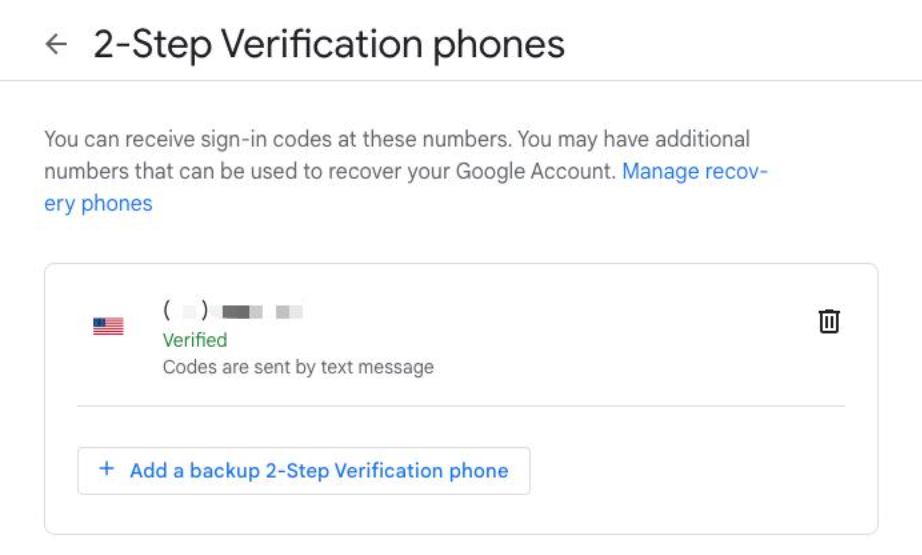
To set up MFA, start by identifying the platforms or services that offer this feature. Websites such as Google, Apple, Microsoft, Slack, PayPal, and Github have MFA options in their security settings. It’s a good idea to enable MFA wherever it’s available by following the on-screen instructions to configure it. Typically, this only takes a few minutes and involves linking your account to your mobile phone number or an authenticator app.
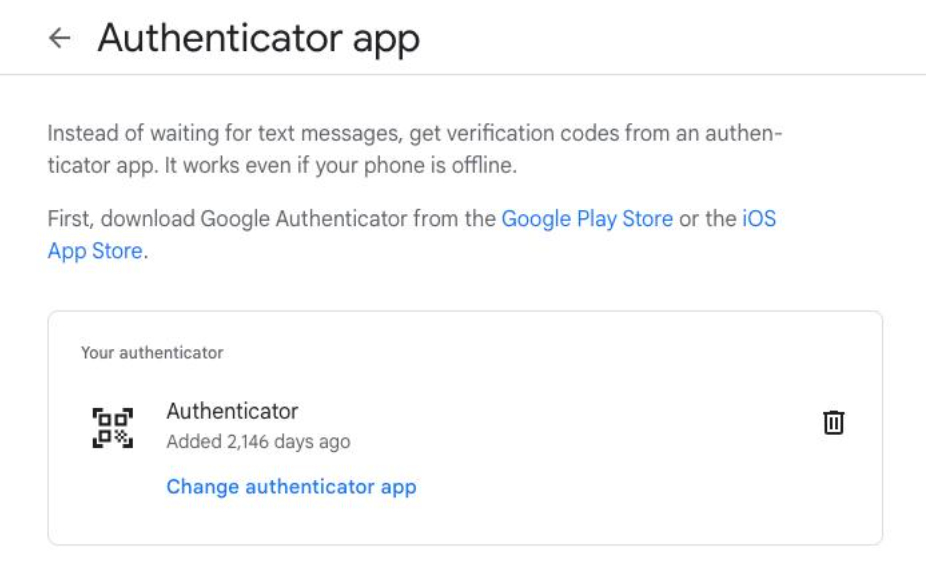
Once MFA is enabled, when you access your account, you’ll be prompted to enter the secondary authentication factor. If using the code option, you’ll receive one via the selected method, and you’ll need to enter it to log in. If using an authenticator app, simply open the app to generate a unique code that will expire after a short period of time.
Things to keep in mind.
To make the most of MFA, it’s recommended to use it across all your online accounts, especially those containing sensitive data like finances, work resources, or personal communications. This ensures consistent protection and minimizes the risk of being compromised through a vulnerable account.
It’s important to note that while MFA significantly improves security, it’s not foolproof. There have been instances where hackers have managed to bypass MFA using sophisticated techniques. Therefore, it’s essential to continue practicing good security habits, such as using strong passwords, keeping software up-to-date, enabling the most secure forms of MFA, and being cautious of phishing attempts.
What’s the bottom line?
Now that you understand what MFA is and why it’s a necessity, it’s time to make it a priority and take action. Though it may be time-consuming to go through all of your applicable work and personal accounts, the extra protection will be well worth it in the long run. Even if you’re someone who reuses the same password across accounts, you can breathe a sigh of relief if those accounts have MFA enabled.
With options like using your phones, apps, and physical keys, MFA lets you balance security and convenience. You can rest assured that your logins and data are protected. Best of all, by combining something you know, have, and are, MFA greatly reduces the risk of unauthorized access to your accounts while improving your user experience.
